Securing TACACS+ by integrating Cisco ISE with Duo
TACACS+ is a Cisco-developed protocol for AAA services. Whereas RADIUS is primarily used to provide AAA services for ...
TACACS+ is a Cisco-developed protocol for AAA services. Whereas RADIUS is primarily used to provide AAA services for users on a network, the main use case for TACACS+ is to provide AAA services for administrators of network devices. Adding a second layer of authentication for access to network devices is highly recommended for any organization that takes cybersecurity seriously. In this blog post, we’ll look at how we can set up MFA authentication using Duo for TACACS+ device administration using ISE and AD.
High-level Overview
At a high level, the flow looks like something like this, except that we are authenticating an individual to a network device (as opposed to a client using AnyConnect), and so we are using TACACS (not RADIUS).
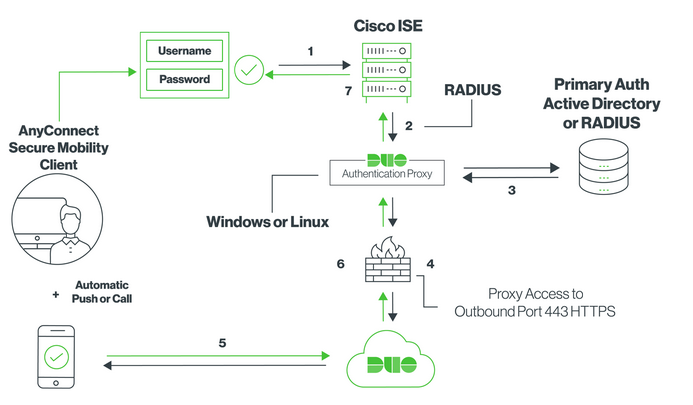
- An administrator attempts to login to a network device using credentials stored on Active Directory. The network device forwards the request to Cisco ISE, which is our TACACS+ server.
- ISE sends the authentication request to Duo’s Authentication Proxy.
- The proxy forwards the request to AD, and AD responds to the proxy.
- Assuming a successful AD authentication, the proxy will send a request to Duo cloud for second-factor authentication.
- Duo sends a push to the device that belongs to the administrator, and he or she responds by approving the push.
- Duo informs the proxy of the successful push, and the proxy informs ISE of the successful authentication.
- Finally, ISE authorizes the administrator to access the network device.
Now let’s look at the details.
Set up the ISE Integration with Duo
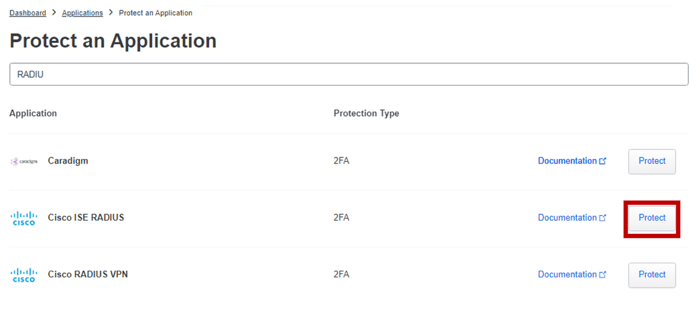
Our first task is to integrate ISE with Duo. To do so, you’ll want to login to the Duo Admin Panel. Navigate to Applications and choose to Protect an Application.
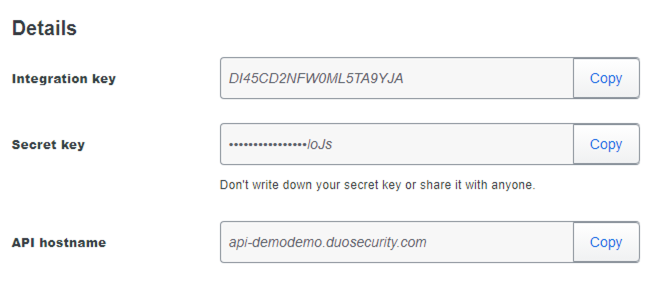
This will generate a set of information - specifically, an Integration Key, a Secret Key, and an API hostname - that we will use to establish the link at the core of our setup between Duo, the Duo Authentication Proxy, ISE, and AD.
Let’s now move to the Authentication Proxy. First, we have to make sure that it can communicate with our AD server. To do this, you’ll need to configure an [ad_client] section in authproxy.cfg. Here’s an example of what it could look like.
[ad_client]
host=198.18.11.1
service_account_username=administrator
service_account_password=C1sco12345
search_dn=DC=dcloud,DC=local
Let’s explain the variables. Host specifies the IP address of your AD server. Service_account_username is the username of an account that has permission to bind to AD and perform searches; service_account_password is that account’s password. Finally, search_dn specifies the LDAP distinguished name of the organizational unit on AD containing all the users you wish to permit to log in.
Next, we’ll want to set up the link between Duo and ISE. To do so, we’ll want to add a [radius_server_auto] section to our authproxy.cfg. Here’s an example of what it could look like.
[radius_server_auto]
ikey=xxxxxxxxxxxxxx
skey=xxxxxxxxxxxxxx
api_host=xxxxxxxxxxxxxx
radius_ip_1=198.18.11.27
radius_secret_1=secret
port=1812
failmode=safe
client=ad_client
The ikey, skey, and api_host values correspond to the Integration Key, a Secret Key, and API hostname values that we made note of earlier in the Duo Admin panel. The radius_ip_1 is where you will specify the IP address of your ISE server, and the radius_secret_1 is the secret that is shared between ISE and Duo. Failmode is an optional parameter that says how to behave if Duo’s server cannot be reached. The safe option says that if Duo cannot be reached, to authenticate the user using only its primary authentication. Finally, client references the mechanism to use to perform primary authentication. Since we are using AD, we specify ad_client.
You can learn more about configuring Duo Authentication Proxy Manager for Cisco ISE here.
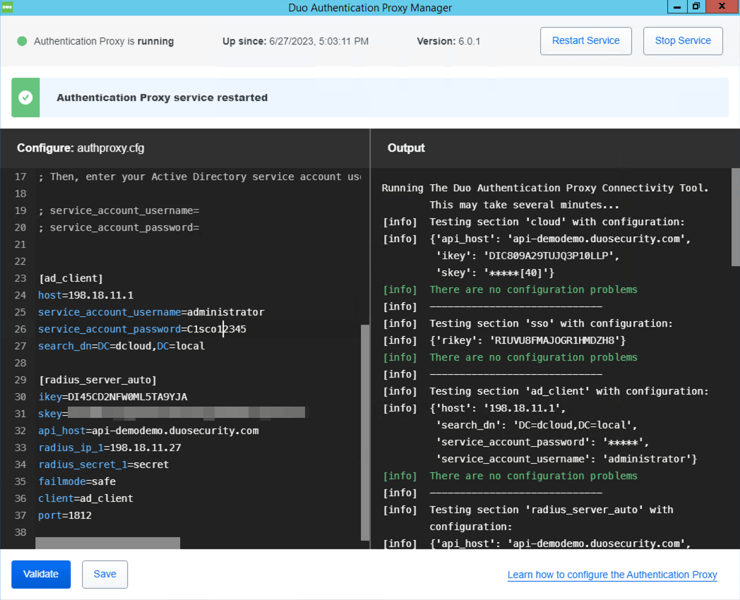
After configuring authproxy.cfg with the specific details in your environment, don’t forget to validate, save, and restart the Proxy.
Setup TACACS Device Administration on ISE
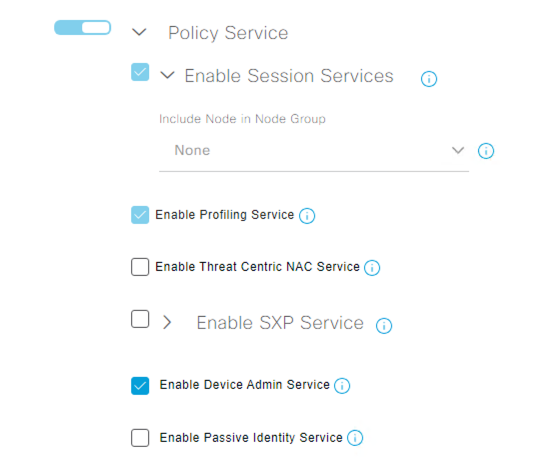
First, we need to enable TACACS on ISE. Navigate to Administration > System > Deployment and select your node. You’ll want to check the Enable Device Admin Service option. If this option is grayed out, it is because you either do not have the appropriate license or have not consumed it yet.
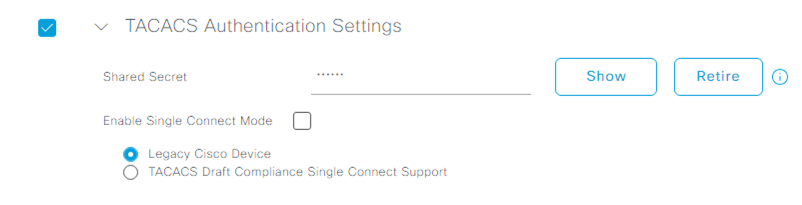
Next, let’s enable TACACS+ on our network devices. In ISE, navigate to Administration > Network Resources > Network Devices. Find the network device you would like to control access to and enable TACACS on it. For the Shared Secret, use the value that you specified in your configuration of the Duo Auth Proxy.
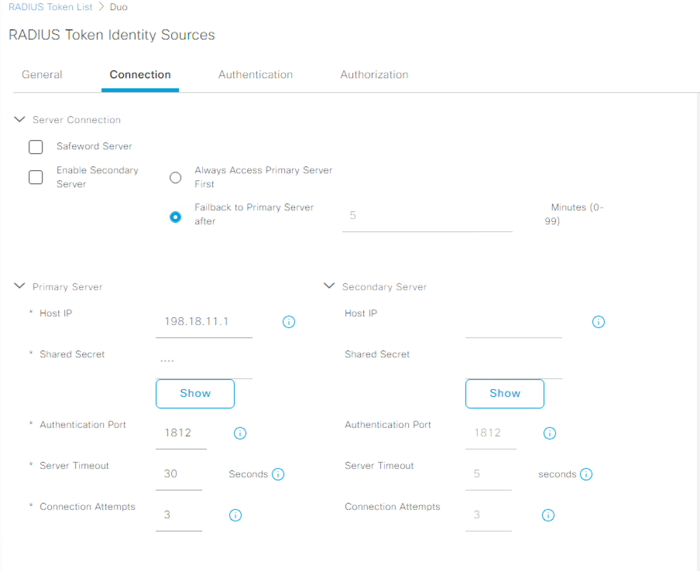
Next, let’s add Duo’s Authentication Proxy to ISE. Navigate to Administration > Identity Management > External Identity Sources. Select RADIUS Token from the left-hand menu to add the Duo connection. Under the Connection tab, you must specify the Host IP address of the Duo Authentication Proxy, as well as the secret you specified in your authproxy.cfg. Finally, it’s important to increase the Server Timeout value so as to give the user time to complete the MFA push.
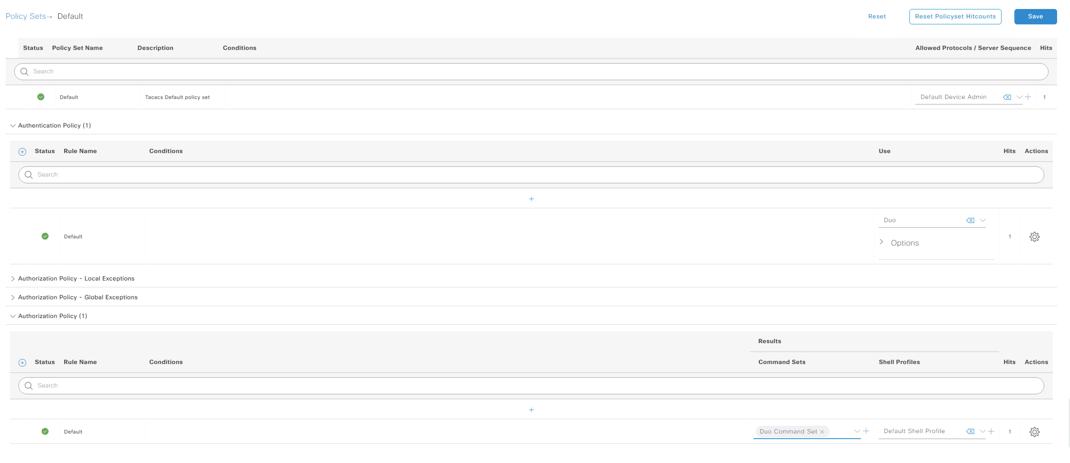
Our final task - navigating to Work Centers > Device Administration > Device Admin Policy Sets - is to write a policy. Precisely how you want to configure your policy will depend on the particularities of your network environment. For demo purposes, we will simply write a policy that authenticates Duo users and authorizes them to perform a Command Set.
Now you should verify your configuration. If all goes according to plan, when you attempt to authenticate to your network device, you will receive a Duo push notification.
Conclusion
Adding a second layer of authentication for network administrators is absolutely necessary for any organization that takes cybersecurity seriously. In the blog post, we looked at how we can use Duo MFA with TACACS+ device administration using ISE and AD.
Questions about configuring Duo or ISE? Schedule some time to speak with one of our cybersecurity experts.