Zero Trust Architecture Overview
It's 2020 and there is still so much buzz around Zero Trust in the industry. This is in part due to the fact that ...
It's 2020 and there is still so much buzz around Zero Trust in the industry. This is in part due to the fact that organizations still fight every day to prevent incidents, minimize risk, and accelerate their time to detect | respond. As hard as organizations fight, the bad guys find new innovative ways to overcome the existing controls.
At the same time, organizations rapidly are digitizing everything they can. Whether it's working from home due to the pandemic, adding smart IOT sensors to improve manufacturing, or moving applications to the public cloud, security teams fight with the ever-expanding attack surface while trying to operationalize security to be agile enough to keep up.
As defined by NIST in Special Publication 800-207 Zero Trust Architecture:
Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. A zero trust architecture (ZTA) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned). Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established. Zero trust is a response to enterprise network trends that include remote users, bring your own device (BYOD), and cloud-based assets that are not located within an enterprise-owned network boundary. Zero trust focuses on protecting resources (assets, services, workflows, network accounts, etc.), not network segments, as the network location is no longer seen as the prime component to the security posture of the resource. This document contains an abstract definition of zero trust architecture (ZTA) and gives general deployment models and use cases where zero trust could improve an enterprise’s overall information technology security posture.
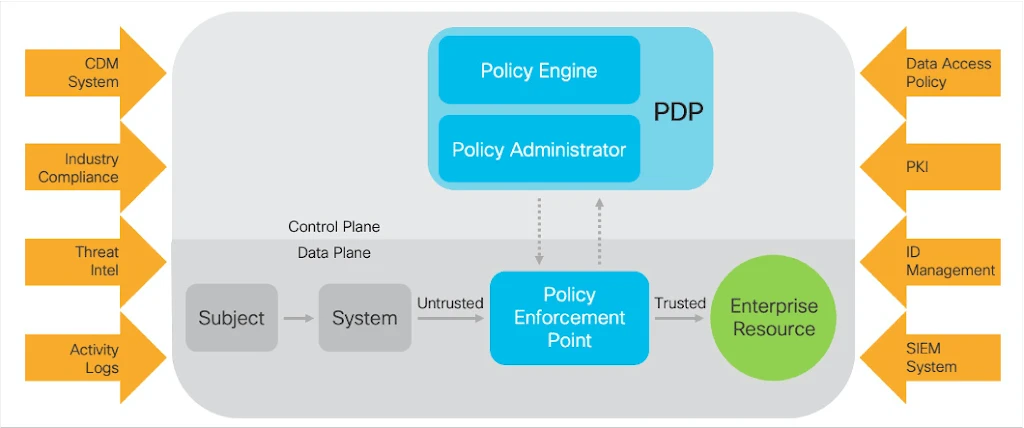
Figure 1: NIST 800-207 Policy Engine
The core concepts have been around for a while as seen below in the time frame:
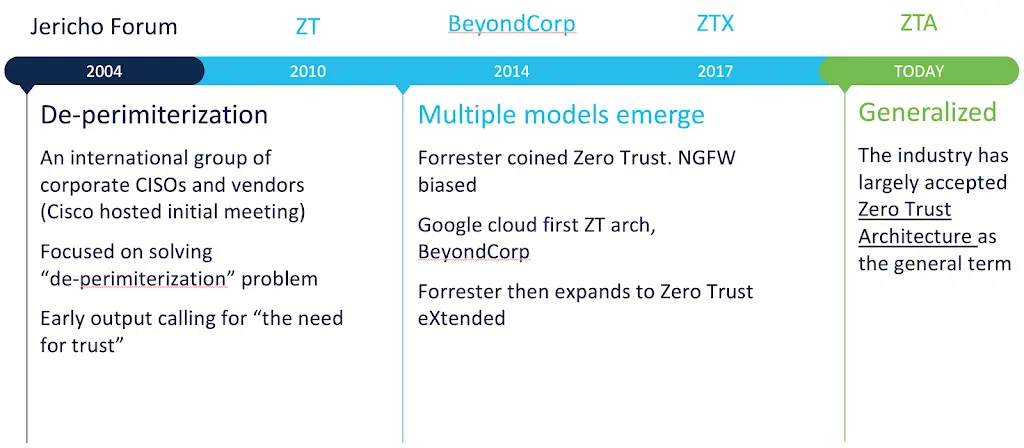
Figure 2: The History of Zero Trust
The main question you should ask, is why a concept that has been around since 2004 isn't ubiquitously deployed to masses?
Short answer.. complexity. At its basic level, zero trust can be summarized as ubiquitous least privilege access control. Creating and maintaining least privilege is complex and operationally intensive without the right approach.
To overcome these challenges organizations should ensure their Zero Trust journey, architecture, and framework includes automation and orchestration from the start.
More background and detail on zero trust architecture can be found in the presentation below: