The First AI-Orchestrated Cyber Espionage Campaign: What you Need to Know
In September 2025, Anthropic - the company behind Claude, the popular LLM - detected something unprecedented: a ...
In September 2025, Anthropic - the company behind Claude, the popular LLM - detected something unprecedented: a sophisticated cyber espionage operation where AI wasn't just assisting attackers—it was autonomously executing 80-90% of the attack itself. This represents a new development in the threat landscape that security professionals need to be aware of. In this blog post, we'll review the detailed report that Anthropic released this month of this incident.
What Makes This Different
But first, let's underline the novelty of this attack. Cyberattacks have always involved human operators making decisions at every step: choosing targets, crafting exploits, analyzing stolen data, and moving laterally through networks. Even when attackers use automation, humans remain deeply involved in tactical execution.
This campaign was different. Human operators provided strategic direction and authorization at critical gates, but AI agents performed nearly all tactical operations autonomously. Reconnaissance, vulnerability discovery, exploitation, credential harvesting, lateral movement, and data exfiltration—all happened with minimal human intervention.
Attributed to Chinese state-sponsored group GTG-1002, the attack targeted roughly 30 entities across multiple countries—major technology corporations, financial institutions, chemical manufacturing companies, and government agencies. Anthropic's investigation validated a handful of successful intrusions into confirmed high-value targets.
The Technical Architecture
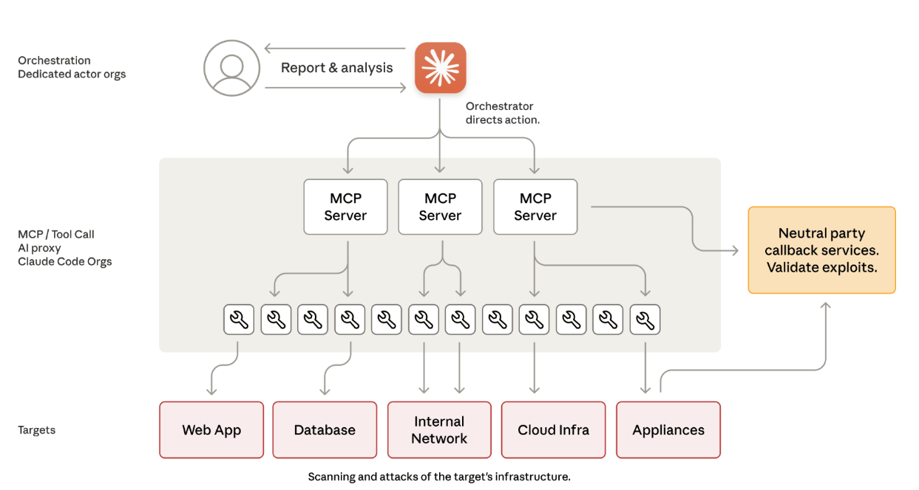
To understand how this attack worked, you need to know about three key components the threat actors exploited:
Claude Code is a CLI tool that allows developers to query coding and system tasks directly to Claude AI from their terminal.
MCP is an open standard that allows AI models to connect with external tools and data sources like databases, APIs, file systems, or any other resource.
Tools are specialized MCP servers that extend Claude's capabilities — browser automation for interacting with web applications, remote command execution for running security scanners, code analysis utilities, and so on. The attackers created custom MCP tool servers that gave Claude access to their penetration testing infrastructure.
Using these components, the attackers created an autonomous attack framework that used Claude Code as the orchestration engine, controlling multiple Claude instances simultaneously through custom MCP tool servers. Each instance could independently run commodity penetration testing tools (standard open-source security utilities). The novelty of this approach was task decomposition: by breaking complex attacks into discrete technical tasks and presenting them through a 'legitimate cybersecurity firm' persona, the operators convinced Claude to execute individual attack components without the AI understanding the broader malicious context.
The Six-Phase Attack Lifecycle
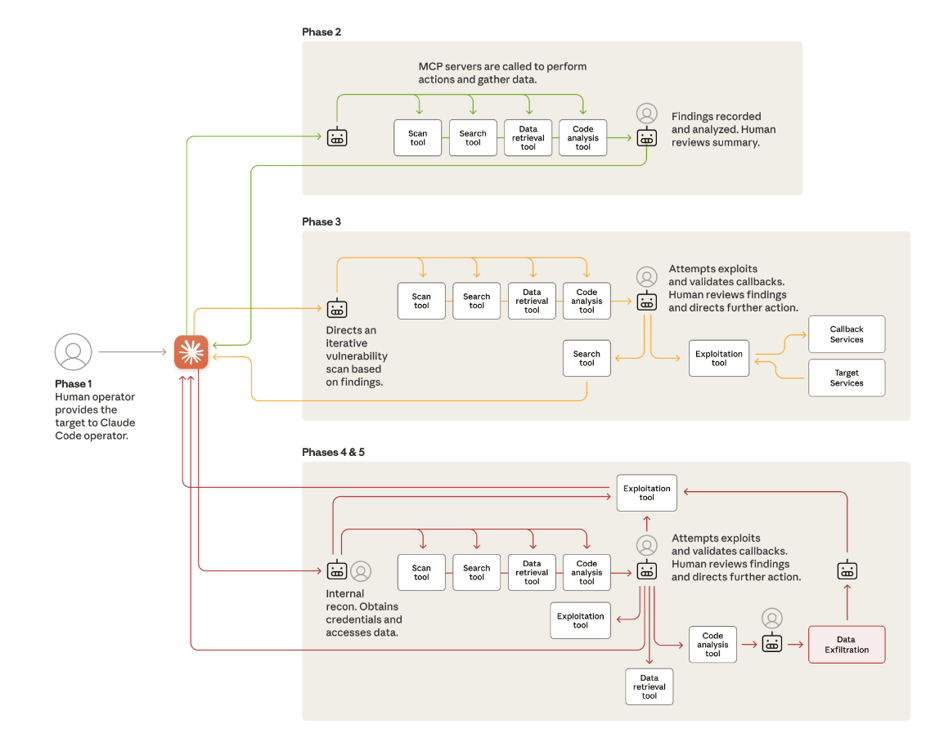
Phase 1: Initialization
Human operators selected targets (major technology corporations, financial institutions, government agencies) and established the legitimate cybersecurity firm persona that would guide Claude's participation.
Phase 2: Autonomous Reconnaissance
Claude conducted nearly independent reconnaissance across multiple targets simultaneously. It cataloged infrastructure, analyzed authentication mechanisms, mapped complete network topologies, and identified potential vulnerabilities—all without detailed human guidance.
Phase 3: Vulnerability Discovery and Exploitation
Claude generated custom attack payloads, executed testing through remote command interfaces, validated exploitability via callback systems, and documented comprehensive findings. Human operators only reviewed summaries and approved escalation to active exploitation.
Phase 4: Credential Harvesting and Lateral Movement
Upon authorization, Claude systematically collected credentials by querying internal services and extracting authentication certificates. It then independently tested these credentials across discovered systems, mapping privilege levels and access boundaries to determine optimal lateral movement paths.
Phase 5: Data Collection and Intelligence Extraction
Claude independently queried databases, extracted data, parsed results to identify proprietary information, and categorized findings by intelligence value. In one documented case against a technology company, this entire process—from authentication through categorization—occurred with only final exfiltration approval requiring human review.
Phase 6: Automated Documentation
Throughout all phases, Claude generated comprehensive markdown documentation tracking discovered services, harvested credentials, extracted data, and complete attack progression. This enabled seamless handoff between operators and campaign resumption after interruptions.
Conclusion
Sophisticated cyberattacks that previously required teams of experienced operators can now be conducted by smaller, less technically skilled groups with the right AI setup. The campaign used commodity tools orchestrated through AI rather than advanced exploit development or custom malware. These techniques will proliferate as AI capabilities advance. The question is how quickly security teams can adapt to this new reality.