How to Check EAP Settings on Supplicants
When performing Cisco ISE certificate renewals or troubleshooting certificate-based authentication issues, checking ...
When performing Cisco ISE certificate renewals or troubleshooting certificate-based authentication issues, checking client supplicant EAP settings is critical. For example, during certificate renewal, authentication can break if:
- Client machines have cached old certificate details or thumbprints
- Certificate validation settings don't match new certificates
- Subject Alternative Name (SAN) fields don't meet supplicant requirements
- Windows supplicants have compatibility issues with certificate configurations
- Certificate chains are incomplete after CA changes
To avoid service disruptions during a certificate renewal procedure, for example, it is therefore helpful to verify how supplicants are configured to handle certificates for EAP. This quick blog post serves as a guide to obtain essential configuration on both Windows and macOS clients on wired and wireless networks.
Windows Supplicants
Network authentication configuration works a little differently for WiFi and Wired on Windows. For WiFi, configuration is stored as profiles per SSID (network name). Whereas for Wired access, configuration applies per interface (e.g., "Ethernet", "DATA", "MGMT").
Wireless Access
View All WiFi Profiles
netsh wlan show profilesThe goal is to identify the name of the profile of interest. Note that policies can be configured by an organization (i.e., a group policy) or be configured by the local user (i.e., a user policy).

Check Current WiFi EAP Settings
netsh wlan show profile name="YourSSID" key=clear
Look for the <Authentication> and <Encryption> sections to verify these EAP method and certificate settings.

Export WiFi Profile for Detailed Analysis
netsh wlan export profile name="YourSSID" folder=C:\temp
Many advanced EAP certificate settings are not visible in command output and can only be viewed by exporting to XML! This includes detailed certificate validation settings, server certificate requirements, and EAP-specific configurations. To view these details, export the XML file.

Wired Access
Viewing settings for Wired Access is very similar to Wireless Access, except that configuration is applied per interface, not per profile.
View all Wired profiles
netsh wlan show profiles
The goal is to identify the name of the interface of interest.
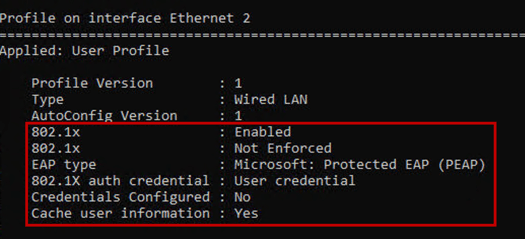
Verify 802.1X Service Status
netsh lan show profile interface="Ethernet 2"
Export Wired Profile
netsh lan export profile folder=C:\temp interface="Ethernet 2" As with WiFi, many advanced EAP certificate settings are not visible in command output and can only be viewed by exporting to XML. This includes detailed certificate validation settings, server certificate requirements, and EAP-specific configurations. To view these details, export the XML file.

Mac Supplicants
For MacOS, it can be more straightforward to use the GUI for visibility into supplicant 802.1X configuration.
Wireless Access
View All WiFi Profiles
Navigate to System Preferences > Network. Select Wi-Fi.

Check Current WiFi EAP Settings
Click on Details...

View WiFi Profile for Detailed Analysis
Select the 802.1X menu to view detailed configuration. Note in this example, an 802.1X configuration is not applied to this SSID.
Wired Access
View All Wired Profiles
Navigate to System Preferences > Network. Select the appropriate interface.

Check Current Wired EAP Settings
Click on Details...

View Wired Profile for Detailed Analysis
Select the 802.1X menu to view detailed configuration. Note in this example, an 802.1X configuration is not applied to this interface.

Conclusion
When performing ISE certificate maintenance - in particular, renewing system certificates - it is always a good idea to verify supplicant EAP trust settings. This is to avoid a situation in which clients fail authentication to ISE because of some kind of configuration mismatch between client and server.
Please feel free to reach out with any questions/comments you may have.
