Should your Security Strategy Employ Defense in Depth, Zero Trust or Both?
I have seen no shortage of articles over the past few years talking about Zero Trust (ZT) and what it means for your ...
I have seen no shortage of articles over the past few years talking about Zero Trust (ZT) and what it means for your security posture and protections. What I have not seen as much of recently is much talk of Defense in Depth (DiD), and when I did it was, in most cases, comparing DiD to ZT. Does that mean DiD is dead? Does zero trust replace the mindset and actions that used to be taken in a DiD strategy? I would argue that the answer is No, they actually can work together and complement each other.
What is Defense in Depth?
Defense in depth is a security strategy that involves deploying multiple layers of security controls to protect a network or system. This can include measures such as firewalls, intrusion detection systems, access control policies, and data encryption. The idea behind defense in depth is to ensure that even if one layer of security fails, there are additional layers in place to provide protection. This can help to prevent unauthorized access, data breaches, and other security incidents that can have serious consequences for your organization. Additionally, defense in depth can help to ensure compliance with industry regulations and standards, which may require the implementation of specific security controls.

Defense in depth is commonly looked at as layers of an onion, with each layer providing additional protection for the network or system.
- Perimeter security:
- This includes measures such as firewalls, intrusion detection and prevention systems, and network segmentation to prevent unauthorized access to the network.
- Access control:
- This involves implementing strong authentication and authorization controls, such as multi-factor authentication and least privilege access, to limit access to network resources only to those users and devices that have been verified and authorized.
- Endpoint security:
- This includes measures such as antivirus software, host-based firewalls, and intrusion detection and prevention systems to protect individual devices from attack.
- Data protection:
- This involves measures such as data encryption, data backup and recovery, and data loss prevention to protect sensitive data from unauthorized access or disclosure.
- Monitoring and response:
- This involves continuous monitoring of network traffic and security events, as well as rapid response to security incidents to minimize the impact of any breaches.
Each layer of the onion provides additional protection for the network or system and helps to reduce the risk of a successful attack. By implementing multiple layers of defense in depth, organizations can better protect their networks and data from cyber threats.
Defense in Depth as a strategy is originally credited to the Roman Army in the 3rd and 4th Centuries AD with the NSA being credited for its use in digital network security in this century. There is certainly is plenty of information out there if you desire more details. However, as you continue reading, remember that the primary outcome of a DiD strategy is to ensure that multiple layers of security exist to cover in the event that a single layer fails. DiD was also traditionally viewed as a perimeter-based strategy, or protections from attacks and threats from outside the "trusted" network.
Let's move on to taking a look at Zero Trust.
What is Zero Trust?
Zero trust is a security model that has gained popularity in recent years due to the increasing number of cyber attacks targeting organizations of all sizes. The traditional security model for network access involves granting access to users and devices that are considered to be "trusted" based on their location, device type, or user credentials. However, this model has proven to be ineffective in preventing advanced persistent threats and other types of cyber attacks.
The zero trust model, on the other hand, assumes that no user, device, or network is inherently trustworthy. Instead, all users, devices, and network traffic must be verified and authenticated before being granted access to network resources. This involves implementing strong identity and access management controls, such as multi-factor authentication and least privilege access, as well as continuous monitoring and inspection of network traffic.
The zero trust model is based on the principle of "never trust, always verify." This means that all users and devices, whether they are inside or outside the network perimeter, must be authenticated and authorized before they are allowed to access any network resources. Authentication involves verifying the identity of the user or device, while authorization involves determining what resources the user or device is allowed to access.
The goal of zero trust is to minimize the risk of unauthorized access and data breaches by limiting access to network resources only to those users and devices that have been verified and validated. This is achieved by implementing a variety of security controls, such as network segmentation, micro-segmentation, and software-defined perimeters. These controls help to limit the attack surface of the network and prevent lateral movement by attackers who have gained access to the network.
Overall, the zero trust model provides a more comprehensive and effective approach to network security than the traditional "trust but verify" model. By assuming that no user, device, or network is inherently trustworthy, and implementing strong authentication and access controls, organizations can better protect their networks and data from cyber threats.
At ModernCyber we utilize any and all of the ZT methodologies and frameworks when assessing a customer's Zero Trust status and strategy. We most commonly leverage the CISA Zero Trust Maturity Model and its pillars as a point of reference. Below you will see the depiction of the control pillars and the foundations that go across all pillars.
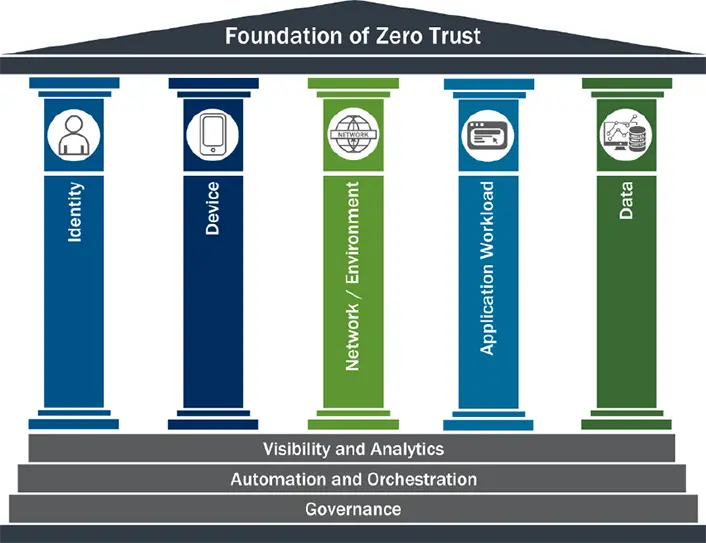
Furthermore, in the CISA model, you will find a mapping of controls to the pillars and the maturity assignment based on the status of the controls in the environment. This mapping is a critical part of assessing the efficacy of the controls in place.
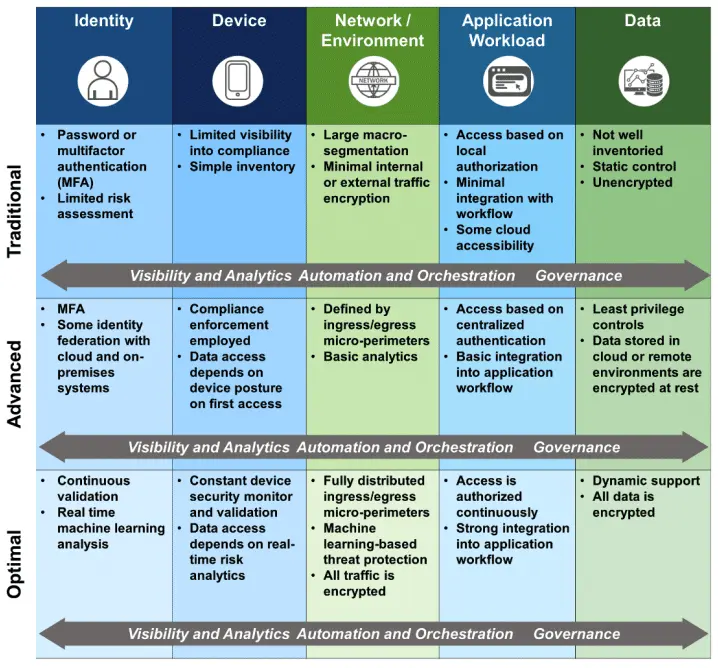
Assessing security efficacy in the ZT mindset requires looking at traffic as it flows from a subject to a resource and identifying the PEP or controls that exist along that flow. Another key item to keep in mind is where and how many PEPs apply policy in the flow.
What should we follow? Zero-Trust or Defense in Depth?
As you can now see, there is a pretty strong alignment of the layers of DiD to the pillars of ZT. At the same time, you can hopefully see that Zero Trust doesn't replace Defense in Depth but I believe it to be a similar and co-existing strategy. Both of these methods have their own unique advantages and disadvantages, and the choice between using either one or both of them depends on the specific needs and goals of each organization.
The idea behind defense in depth is to make it as difficult as possible for an attacker to penetrate the network. By implementing multiple layers of security, organizations can create a more holistic approach to security. On the other hand, zero trust is a security model that assumes that no user or device should be trusted by default, even if they are inside the network perimeter. This means that all access requests are verified and authenticated before being granted. Zero trust also involves implementing strict access controls and monitoring all network activity for potential threats. The goal of zero trust is to prevent unauthorized access to the network and to limit the potential damage that can be caused by an attacker internal or external.
While both defense in depth and zero trust have their own advantages, they also have their own disadvantages. Defense in depth can be expensive and complex to implement, as it requires multiple layers of security and can be difficult to manage. On the other hand, zero trust can also be difficult to implement and may require significant changes to the network architecture. However, zero trust is generally more focused on preventing unauthorized access through identity and can be more effective at limiting the potential damage caused by an attacker.
Ultimately, the choice between defense in depth and zero trust depends on the specific needs of each organization. Some organizations may find that a combination of both approaches works best for their particular security needs. For example, they may implement defense in depth & zero trust for their most critical systems and use only zero trust for less critical systems. Other organizations may find that one approach works better for them than the other. Whatever the case, it is important for organizations to carefully consider their security needs, risk profile, risk tolerance, and goals when choosing a security strategy.
ModernCyber's Zero Trust Assessment
Whether you're just starting, in the midst, or completed your zero trust journey, ModernCyber's Zero Trust Assessment evaluates your current zero trust architecture and capabilities for all zero trust domains.
Schedule some time to speak with one of our cybersecurity experts.